- blog
- Statistics
- Business Email Compromise Statistics 2025 | Latest BEC Trends & Data

Business Email Compromise Statistics 2025: The Ultimate Guide for BDRs & AEs
Table of Contents
Picture this: You’re a BDR crushing your quotas, responding to what looks like an urgent email from your CEO about a “confidential client payment.” Thirty minutes later, you realize you’ve just helped transfer $50,000 to a scammer’s account. Sound far-fetched? Unfortunately, business email compromise attacks like this are becoming alarmingly common.
As sales professionals, you live in your inbox—building relationships, closing deals, and managing client communications. But this digital lifestyle also makes you prime targets for sophisticated email scams that can cost your company millions and destroy your hard-earned reputation.
This comprehensive guide breaks down the latest business email compromise statistics, reveals how these attacks work, and shows you exactly how to protect yourself and your organization in 2025.
What You Need to Know About BEC Attacks
Business email compromise (BEC) is a sophisticated cyberattack where criminals impersonate trusted contacts—like executives, clients, or vendors—to trick employees into transferring money or sharing sensitive information. Unlike typical phishing emails with suspicious links or attachments, BEC attacks rely purely on psychological manipulation and social engineering.
Business email compromise attacks accounted for 73% of all reported cyber incidents in 2024, making them one of the most prevalent threats facing organizations today.
The Five Main Types of BEC You Should Know
Understanding how attackers operate helps you spot red flags before it’s too late:
CEO Fraud (Executive Impersonation): Scammers pose as high-level executives requesting urgent wire transfers or sensitive data. In over 60% of phishing emails, attackers impersonate a well-known brand or entity to exploit existing trust.
Account Compromise: Attackers gain access to legitimate email accounts and use them to send fraudulent requests. This is particularly dangerous because emails come from genuine, trusted addresses.
Vendor Email Compromise: Criminals impersonate suppliers or business partners, often requesting payment to “updated” bank accounts.
Attorney Impersonation: Scammers pose as lawyers, using urgency and confidentiality to pressure victims into quick action.
Data Theft: Rather than seeking immediate payment, attackers target valuable business information, including CRM data that sales teams handle daily.
Why This Matters for Sales Teams: As BDRs and AEs, you’re communication hubs handling client data, payment information, and confidential deal details. Your compromised account could become a weapon against your entire client base.
Key BEC Statistics for 2025
The numbers tell a sobering story about the business email compromise threat landscape. Here’s what security experts and law enforcement agencies are reporting:
Staggering Financial Losses
In 2024 alone, BEC losses totaled $2.77 billion across 21,442 reported incidents, making it the second-costliest type of cybercrime after investment scams.
$6.7 billion was lost globally to BEC, making it the costliest cybercrime according to industry estimates. To put this in perspective, IC3 data shows the BEC scam has been reported in all 50 states and 186 countries.
The average loss per victim data shows that fewer people and organizations are being scammed out of larger amounts per incident, with the average cost per complaint increasing from $74,723 in 2019 to $137,132.03 in 2023.
Attack Frequency That Should Alarm You
Organizations with 50,000 employees or more have a nearly 100% chance of experiencing at least one BEC attack every week. But don’t think smaller companies are safe—even organizations with fewer than 1,000 employees have a 70% weekly probability of experiencing at least one BEC attack.
In 2023, BEC attacks skyrocketed, with monthly attacks per 1,000 mailboxes more than doubling to 10.77, a staggering 108% increase compared to 2022.
The Median Hit Per Incident
When BEC attacks succeed, the financial damage is substantial. The average amount lost per BEC attack was higher, at just over $125,600—a 300% increase since 2015.
The average BEC wire transfer request was $24,586 at the start of 2025, though many attacks target much larger amounts.
🔥 Protect Your Sales Pipeline
Secure Your Cold Email Operations
Don’t let BEC attacks compromise your outreach efforts. Salesso provides verified cold email addresses and secure sending infrastructure.
Analysis: What Do the Current BEC Trends Tell Us?
The business email compromise landscape is evolving rapidly, driven by technological advances and changing attacker strategies. Here’s what the data reveals about where threats are heading:
The AI Revolution in BEC Attacks
By mid-2024, an estimated 40% of BEC phishing emails were AI-generated. This represents a fundamental shift in how attacks are crafted and deployed.
49% of detected spam emails are categorized as BEC emails, and 40% of BEC emails are generated by AI, according to recent threat intelligence reports.
Since the popularisation of generative AI tools, BEC has gone from being only 1% of all cyber attacks in 2022 to 18.6% of all attacks.
The implications are serious: AI allows attackers to create perfect grammar, compelling narratives, and personalized content at scale—making traditional “look for spelling errors” advice obsolete.
Conversation Hijacking on the Rise
Scammers are increasingly infiltrating real email threads, a technique called conversation hijacking that’s particularly dangerous for sales teams managing complex deal communications.
Here’s how it works: Attackers compromise an email account, monitor legitimate business conversations, then insert themselves into ongoing threads with fraudulent requests that seem contextually appropriate.
Multi-Channel Attack Evolution
Modern BEC attacks aren’t confined to email. Vishing attacks are growing in prevalence, with 30% of organizations reporting instances where threat actors used fake calls to impersonate officials or executives.
We’re now starting to see more blended attacks where an email sets up a phone call, or a text message preys on urgency.
Industry Targeting Patterns
The manufacturing sector bore the brunt (25%) of email attacks in the quarter, followed by retail (20%) and real estate (11%). However, no industry is immune—attackers target sectors they perceive as having weaker cybersecurity defenses.
Case Studies: Notable BEC Incidents
Real-world examples show how devastating business email compromise can be, even for sophisticated organizations:
The Facebook and Google Mega-Scam (2013-2015)
The biggest BEC scam of all time was a VEC attack against tech giants Facebook and Google that resulted in around $121 million in collective losses. The attacker impersonated Quanta Computer, a legitimate hardware supplier, sending fake invoices that appeared completely legitimate.
Key Lesson: Even tech giants with advanced security can fall victim to well-crafted impersonation attacks.
The €220,000 Deepfake Voice Scam (2024)
LastPass noted over $200 million in losses in 2025 attributed to deepfake fraud involving authority figures. In one case, a finance chief transferred €220,000 after receiving a phone call with what sounded exactly like the CEO’s voice, but was actually an AI-generated deepfake.
Key Lesson: Voice verification alone is no longer sufficient—independent verification through separate channels is essential.
Manufacturing Company Loses $60 Million (2024)
A global manufacturing company lost $60 million when an employee was tricked into making multiple fraudulent wire transfers through sophisticated social engineering.
Key Lesson: Anyone with access to financial processes can be targeted, regardless of their role or seniority level.
The Psychology Behind BEC Attacks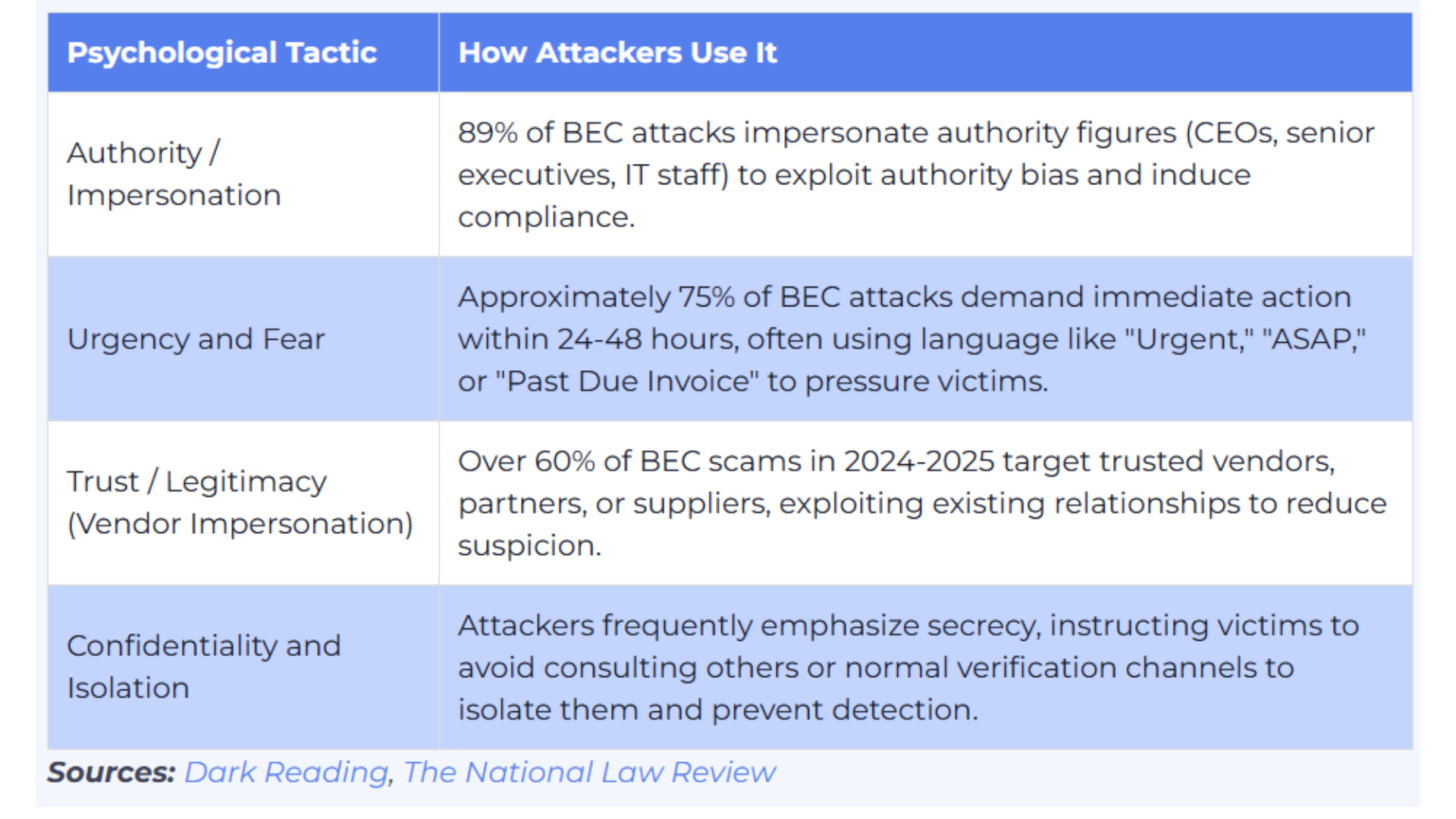
Understanding the psychological tactics attackers use is crucial for building mental defenses against manipulation:
Authority Exploitation
Many BEC emails alter the display name to pose as a high-ranking person – this was observed in 36% of BEC emails in one study. People naturally comply with requests from perceived authority figures, often without questioning.
Urgency and Pressure Tactics
Gift card scams are one of the most common social engineering tactics. In Q1 of 2024 alone, 37.9% of BEC incidents were gift card schemes. Attackers create artificial deadlines and crisis scenarios to bypass rational thinking.
Trust and Social Proof
Verizon’s data also shows that pretexting (the tactic at the heart of BEC) nearly doubled in frequency last year. Attackers leverage existing business relationships and established communication patterns to appear legitimate.
The Isolation Tactic
Attackers often instruct victims to keep requests “confidential” or “urgent,” preventing them from seeking verification from colleagues who might spot the scam.
Effectiveness of Social Engineering Techniques
The success rates of these psychological manipulation tactics are alarmingly high:
44% of phishing emails were sent from compromised accounts, helping them bypass authentication protocols. When emails come from legitimate, trusted addresses, recipients are far more likely to comply with requests.
94% of organizations fell victim to phishing attacks, up from 92% in 2023, showing that even with increased awareness, social engineering remains highly effective.
95% of cybersecurity leaders revealing that they feel stressed about email security – phishing being their main concern.
📊 Boost Your Email Performance
Advanced Email Analytics & Deliverability
Track your email performance and avoid spam filters with Salesso’s email warming and analytics tools.
Evolution of BEC Tactics: What’s Changed?
Business email compromise attacks have evolved significantly from their early days. Here’s how attackers have adapted their methods:
From Templates to AI-Generated Content
Traditional BEC attacks relied on templates and scripts, making them easier to detect. Previously, many cybercriminals relied on templates to launch their BEC campaigns. However, generative AI tools like ChatGPT let scammers craft unique, perfectly written, and highly targeted content instantly.
Account Takeover vs. Spoofing
Rather than just spoofing email addresses, attackers now focus on compromising legitimate accounts. Thread hijacking attacks typically start with account compromise, allowing attackers access to the inbox to begin searching for ongoing conversations about payments or other sensitive information.
Targeting Evolution
Attackers commonly use services like Gmail to spoof identities, but they’re also becoming more sophisticated in their targeting. By leveraging information on LinkedIn, SEC disclosures, and even the target organization’s website, cybercriminals can create convincing emails that are more likely to trick employees.
Technical Sophistication
A notable trend is the rise in CAPTCHA-based attacks using CloudFlare, which conceal credential harvesting forms from security systems. Attackers are using legitimate services to hide their malicious activities.
Regulatory and Insurance Landscape for BEC in 2025
The legal and insurance environment around business email compromise is becoming increasingly complex:
Key Regulatory Developments
DMARC Enforcement: This marks a continued year-over-year increase in regulatory requirements for email authentication. Companies must implement proper email security protocols or face deliverability issues with their legitimate communications.
Data Breach Notification Requirements: When BEC attacks result in data theft, companies must notify affected individuals and regulators within specific timeframes, often 24-72 hours.
Industry-Specific Requirements: Financial services, healthcare, and other regulated industries face additional compliance obligations when handling BEC incidents.
Cyber Insurance Challenges
Insurance coverage for BEC is becoming more restrictive and expensive:
- Higher Premiums: Due to the frequency and cost of BEC claims, premiums have risen significantly
- Stricter Underwriting: Insurers now require specific security measures before providing coverage
- Limited Coverage: Standard policies increasingly exclude BEC unless specific endorsements are purchased
- Proof of Due Diligence: Claims can be denied if companies can’t prove they followed proper verification procedures
Business Email Compromise Prevention Strategies
Protecting your organization from BEC requires a multi-layered approach combining technology, processes, and human awareness:
Technical Defenses
Email Authentication (DMARC, SPF, DKIM): These protocols help prevent domain spoofing and improve email deliverability for legitimate messages.
Multi-Factor Authentication (MFA): Essential for protecting email accounts, CRM systems, and other business applications.
Advanced Email Security: AI-powered email filters that can detect suspicious patterns and anomalies in communication.
Secure CRM Practices: Protecting customer data and contact information from unauthorized access.
🛡️ Advanced Email Security
Protect Your Business Communications
Implement robust email security measures with Salesso’s enterprise-grade protection and monitoring tools.
Process Controls
Verification Protocols: Mandatory callback procedures for any financial requests or banking changes, using previously known contact information.
Dual Approval: Requiring two-person authorization for significant financial transactions or sensitive data changes.
Segregation of Duties: Ensuring different people handle payment initiation, authorization, and execution.
Regular Training: Ongoing education about BEC tactics and red flags to watch for.
Human Firewall Training
Red Flag Recognition: Teaching employees to identify urgent requests, unusual communication patterns, and pressure tactics.
Verification Habits: Creating automatic responses to double-check any financial or sensitive requests through independent channels.
Incident Reporting: Clear procedures for reporting suspicious emails without fear of punishment.
Simulated Attacks: Regular testing with fake BEC scenarios to measure and improve response rates.
Specific Strategies for Sales Teams
CRM Security: Use strong, unique passwords and enable MFA for customer relationship management systems.
Client Communication Protocols: Establish secure channels for discussing sensitive deal information and payment details.
Email Signature Verification: Be suspicious of any changes in email signatures, especially for financial communications.
Deal Verification: Confirm any last-minute changes to payment terms or banking information through phone calls to known numbers.
What to Do If You Suspect a BEC Attack
Quick action can make the difference between a near-miss and a major financial loss:
Immediate Response Steps
- Don’t Delete the Email: Preserve evidence for investigation
- Don’t Reply: Avoid confirming your email is active
- Alert IT Security: Report the incident through official channels immediately
- Document Everything: Screenshot the email and note any related communications
If Money Was Transferred
- Contact Your Bank Immediately: Request a recall of funds and provide necessary documentation
- File a Police Report: Local law enforcement can help with recovery efforts
- Report to FBI IC3: File a complaint at ic3.gov for federal investigation
- Notify Your Insurance Company: Begin the claims process if you have cyber insurance
Recovery Actions
- Change Passwords: Update credentials for potentially compromised accounts
- Review Account Activity: Check for unauthorized access or changes
- Enhance Security: Implement additional protection measures
- Conduct Training: Use the incident as a learning opportunity for your team
Conclusion
Business email compromise represents one of the most serious cybersecurity threats facing organizations today. With $2.77 billion in losses reported in 2024 and 40% of BEC phishing emails now AI-generated, the threat landscape is more dangerous than ever.
For BDRs and AEs, understanding these business email compromise statistics isn’t just about cybersecurity—it’s about protecting your career, your clients, and your company’s future. The convergence of AI-powered attacks, sophisticated social engineering, and the high-value nature of sales communications creates a perfect storm of risk.
The key takeaways for sales professionals:
- Verify Everything: Always confirm financial requests through independent channels
- Trust Your Instincts: If something feels off, it probably is
- Stay Informed: Keep up with the latest BEC tactics and trends
- Implement Security: Use MFA, strong passwords, and secure communication practices
- Report Suspicious Activity: Quick reporting can prevent major losses
🚀 Scale Your Outreach Safely
Complete Cold Email Solution
From verified email addresses to secure sending infrastructure, Salesso provides everything you need for successful cold email campaigns.
Remember, cybercriminals are constantly evolving their tactics, but with proper awareness, training, and security measures, you can stay one step ahead. The cost of prevention is always less than the cost of a successful attack.
Frequently Asked Questions
What is the difference between BEC and regular phishing?
How can I verify if an urgent email request is legitimate?
What should I do if I accidentally responded to a BEC email?
Are small companies really at risk for BEC attacks?

Find Quality Leads in Just One Click
Install SalesSo’s Chrome Extension and start collecting leads while you browse your favorite sites
